What Are Proxies For: A Complete Guide to the Purpose, Advantages, and Use of Proxy Servers
In today's digital world, where issues of privacy, data security, and optimized internet connections are becoming increasingly important, understanding what proxies are for is of paramount importance. Proxy servers allow you to hide your real IP address, bypass blocks, improve connection speeds, and provide anonymous access to the internet. In this guide, we will thoroughly examine the functions and benefits of proxies, their role in data protection, as well as provide practical recommendations for selecting and configuring them. If you want to know why proxies have become an indispensable tool for both businesses and private users, this article will give you comprehensive information and help you make the right choice.
Introduction: Why Proxies Play a Key Role in the Modern Internet
In the age of globalization and constant online information exchange, users face threats of data breaches, cyberattacks, and access restrictions. Proxy servers act as intermediaries, providing an extra layer of protection, optimizing connections, and allowing you to bypass censorship. What are proxies for? They help protect personal and corporate data, maintain anonymity while online, and ensure stable access to necessary resources even if they are blocked or restricted in certain regions.
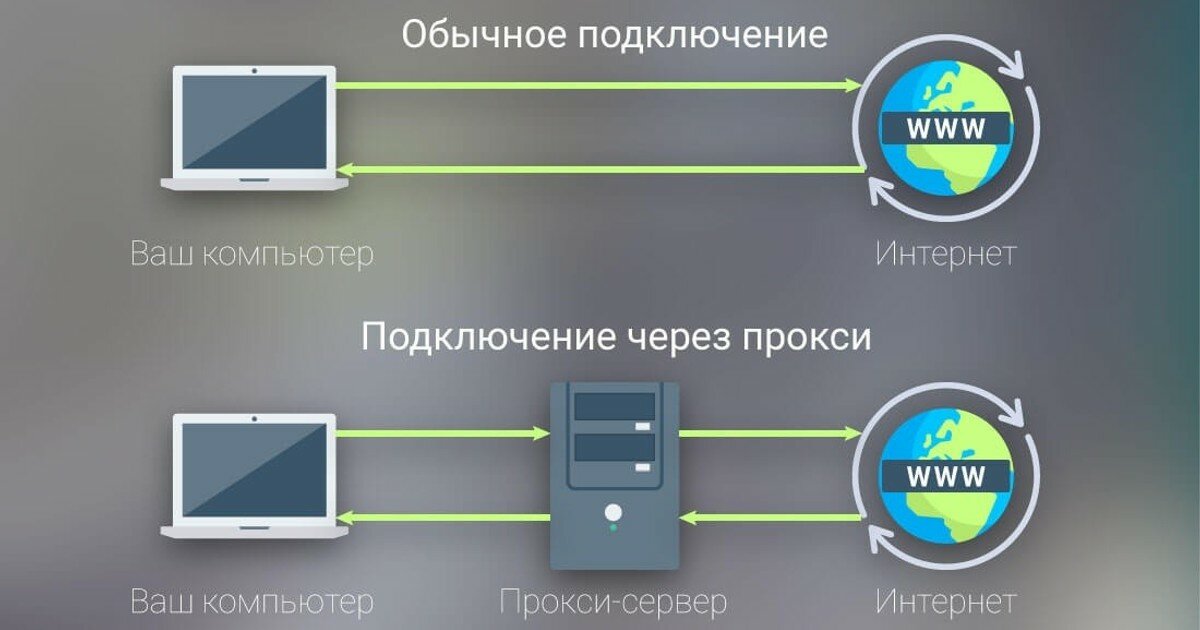
What Is a Proxy Server and How Does It Work
A proxy server is a computer or software that acts as an intermediary between your device and online resources. It receives requests from the user, forwards them to target servers, and returns the retrieved data. The main functions of a proxy include:
- Hiding the IP Address: The proxy replaces your real IP address with its own, increasing your level of anonymity.
- Caching Data: Some proxy servers can store copies of requested resources, speeding up the loading of repeat requests.
- Filtering and Access Control: Proxies allow you to block unwanted content or restrict access to certain sites.
- Bypassing Restrictions: Using a proxy helps you access resources that are blocked at the ISP or regional level.
Thus, what are proxies for can be answered: they are a multifunctional tool that provides anonymity, security, and optimization for internet usage.
Main Types of Proxy Servers
There are several main types of proxy servers available, each with its own features and intended use. Let’s take a closer look:
HTTP and HTTPS Proxies
These proxy servers work with web traffic, redirecting HTTP requests. HTTPS proxies provide additional encryption for data, which is especially important when transmitting confidential information.
SOCKS Proxies
SOCKS proxies support the transmission of all types of data, including TCP and UDP, and are used for more versatile tasks such as P2P networks, online gaming, and VOIP. They do not interfere with the content being transmitted, which makes them highly versatile.
Residential Proxies
Residential proxies use real IP addresses provided by internet service providers. They appear natural to target services and are more difficult to block. This type of proxy is especially useful for bypassing sophisticated filters and ensuring a high level of anonymity.
Data Center Proxies
Data center proxies are based on virtual IP addresses located in professional data centers. They offer high speed and stable connections, making them ideal for tasks that require rapid data transmission, such as scraping and streaming.
Mobile Proxies
Mobile proxies use IP addresses from mobile operators, allowing access to content optimized for mobile devices and bypassing blocks typical of fixed networks. They are particularly relevant for testing mobile applications and running marketing campaigns targeted at mobile users.
Advantages of Using Proxy Servers
Now that we have discussed what proxies are for and the types that exist, let’s review the main benefits of using them:
- Anonymity and Confidentiality: Hiding your real IP address helps protect your personal information and prevents your online activity from being tracked.
- Bypassing Blocks: Proxies allow you to access websites and services that may be restricted by geographic location or censorship.
- Optimized Speed: Using caching and proper traffic routing improves webpage loading times and reduces latency.
- Protection Against Cyberattacks: An additional layer of protection provided by proxies helps minimize the risk of data leaks and enhances network security.
- Flexibility and Scalability: Proxy servers can be easily adapted for various tasks—from personal use to corporate solutions—ensuring high performance and accessibility.
Key Criteria for Choosing a Reliable Proxy
The answer to the question “how to choose a reliable proxy” depends on several key criteria that will help ensure the quality, speed, and security of the chosen solution. Let’s review the main factors:
1. Connection Speed
One of the most important factors is the connection speed. A reliable proxy should provide fast response times and stable data transmission. To evaluate speed, it is recommended to use specialized online tools that measure server response times and bandwidth.
2. Level of Anonymity and Security
Data protection is a top priority when using proxy servers. Ensure that your chosen proxy effectively hides your real IP address, uses modern encryption and protection methods, and that the provider follows a strict privacy policy and does not log user activity.
3. Stability and Reliability
A reliable proxy must operate without interruptions and provide a stable connection. Key aspects include:
- Systems for redundancy and load balancing;
- Minimal downtime and 24/7 accessibility;
- Responsive technical support from the provider.
4. Geographic Coverage
Choosing servers located in the necessary regions allows you to optimize connection speed and access geographically restricted content. Consider the number of servers available in your target regions, the option to select a specific server location, and the speed and latency metrics for those servers.
5. Cost and Tariff Plans
While quality and security are top priorities, it is also important to consider the service cost. A reliable proxy should offer a reasonable balance between price and quality. Look for flexible tariff plans that allow you to scale the service as your needs grow, a trial period for service evaluation before committing to a long-term contract, and any discounts or special offers for regular customers.
6. Provider Reputation and User Reviews
Research the provider’s reputation and user feedback, as these are key indicators of the service’s reliability. Check independent reviews, the provider’s history in the market, and ratings regarding the quality of technical support and server stability.
Practical Guide to Choosing and Using a Proxy
To answer the question “how to choose a reliable proxy” and maximize its benefits, follow these steps:
Step 1: Define Your Goals and Tasks
Clearly define the tasks for which you need a proxy server. This may include:
- Ensuring anonymous internet access;
- Bypassing geographic blocks and censorship;
- Data scraping and analytics for marketing research;
- Protecting personal and corporate information;
- Optimizing webpage loading speeds.
A clear understanding of your objectives will narrow your search and help you choose the optimal solution.
Step 2: Research the Market and Analyze Offers
Conduct an analysis of various HTTP proxy providers by comparing their tariffs, technical specifications, and user reviews. This will give you an objective view of the quality of services and help you select the most suitable option.
Step 3: Test the Selected Services
Before finalizing your choice, test the proxy servers:
- Measure connection speed and response times using specialized tests;
- Evaluate stability over an extended period;
- Ensure that your real IP address remains hidden and that the encryption level meets your requirements;
- Compare the test results with the data provided by the supplier.
Step 4: Configure and Integrate into Your System
After selecting the optimal service, configure the proxy server according to your needs:
- Set up connection parameters (IP address, port, protocol);
- Integrate the proxy server with your applications and browsers;
- If available, configure automatic IP rotation to enhance anonymity.
Step 5: Monitor and Optimize Performance
Once the service is implemented, it is important to regularly monitor its performance:
- Conduct regular speed and stability tests;
- Monitor user feedback and promptly address any issues;
- Update settings and software to maintain maximum efficiency.
Benefits for Business and Personal Use
A reliable proxy server is useful for both corporate clients and private users:
- For Business: It ensures the protection of confidential data, optimizes access to corporate resources, and enhances the performance of IT systems.
- For Personal Use: It protects personal information, enables bypassing censorship, and provides fast access to necessary resources, thereby enhancing privacy and comfort while using the internet.
- Versatility: Proxy servers easily integrate with various platforms and applications, making them a universal solution for a wide range of tasks.
Advantages of Combining Proxies with Other Technologies
To achieve the best results and maximum protection, it is beneficial to combine the use of proxies with other technologies:
- VPN: Using VPNs in conjunction with proxies provides an extra layer of encryption and increases anonymity, which is particularly important for corporate users.
- IP Rotation: Automatic IP rotation through proxies helps avoid blocks and ensures a continuously updated connection.
- Caching: Technologies that cache data can significantly speed up access to frequently visited resources and reduce network load.
- Integration with Monitoring Systems: This allows for prompt detection and resolution of any issues, enhancing overall efficiency.
Case Studies of Successful Proxy Implementation
Below are some examples of real-world use of reliable HTTP proxies that demonstrate their effectiveness:
Case 1: Optimizing Websites and Data Scraping
A marketing agency specializing in SEO analytics used HTTP proxies to collect data from various websites. Thanks to a reliable and fast connection, the agency was able to bypass regional blocks, analyze competitor rankings, and optimize advertising campaigns. The result was improved marketing strategies and better search engine rankings for their clients.
Case 2: Protecting Corporate Networks
A large company working with confidential data integrated an HTTP proxy to provide secure remote access to corporate resources. The service helped hide internal IP addresses and added an extra layer of protection, reducing the risk of cyberattacks and data breaches.
Case 3: Testing and Developing Web Applications
A web development company used HTTP proxies to simulate user activity from different regions during testing. This allowed them to identify and eliminate bottlenecks, optimize application performance, and increase end-user satisfaction.
Case 4: Anonymous Browsing and Censorship Bypass
A private user seeking to protect personal information and maintain anonymity used an HTTP proxy to bypass regional blocks and hide their real IP address. This enabled safe content viewing, secure social media use, and financial transactions without the risk of data leaks.
Problems and Limitations of HTTP Proxies
Despite many advantages, using HTTP proxies may come with some limitations:
- Low Speed Under High Load: With many simultaneous connections, the speed may drop due to server overload.
- Limited Support for Non-Standard Protocols: HTTP proxies are primarily designed for web traffic, which can restrict their use for some specialized tasks.
- Risk of Data Leaks: Insufficient encryption or misconfiguration may lead to the leakage of confidential information.
- IP Blocking: Some web services actively block known proxy server IP addresses, reducing content accessibility.
Future Trends in HTTP Proxy Development
Given the growing demands for security and performance, HTTP proxy technologies continue to evolve. Key future trends include:
- Enhanced Security Measures: Implementation of modern encryption algorithms and automatic IP rotation will increase data protection and anonymity.
- Optimization of Speed and Stability: The use of artificial intelligence to analyze server load and select optimal data routes will reduce latency and improve connection speeds.
- Integration with Cloud Services: Cloud-based solutions will provide flexibility, scalability, and high availability, adapting proxy services to rapidly changing market demands.
- Expanded Functionality: Adding features such as caching, content filtering, and real-time analytics will make HTTP proxies even more versatile tools for both business and personal use.
- Improved User Experience: Continuous enhancements in interfaces and customer support will allow users to integrate and configure proxies more quickly and efficiently.
Conclusion: The Final Strategy for Choosing a Reliable Proxy
Choosing a reliable HTTP proxy is a critical step in ensuring security, anonymity, and optimal internet performance. The answer to “how to choose a reliable proxy” lies in carefully analyzing key criteria such as connection speed, encryption level, stability, geographic coverage, tariff plans, and the provider’s reputation. A well-chosen HTTP proxy will:
- Protect personal and corporate data through high anonymity;
- Bypass regional blocks and censorship, providing unrestricted access to content;
- Optimize connection speed and stability, which is crucial for business processes and online entertainment;
- Reduce operational costs through flexible tariff plans and scalability.
When selecting and configuring an HTTP proxy, it is important to regularly test, update your software, and keep up with new security trends. A comprehensive approach to integrating HTTP proxies into your IT infrastructure will ensure a secure, fast, and reliable connection – the foundation for success in today’s digital world.
Conclusions
Thus, the benefits of using http-proksi are clear: reliability, speed, anonymity, and flexibility make them an indispensable tool for both businesses and personal use. A wise choice and proper configuration of an HTTP proxy server will allow you to:
- Protect your real IP address and secure confidential information;
- Bypass censorship and geographic restrictions;
- Optimize connection speed and stability;
- Improve workflow efficiency and reduce operational costs.
A proper choice and configuration of an HTTP proxy are the foundations for successful operation in an environment with ever-growing demands for speed and security. Investing in quality solutions is a strategic move that ensures competitiveness and protects both personal and corporate data. The answer to “how to choose a reliable proxy” becomes the basis for building a secure IT infrastructure capable of meeting the needs of even the most demanding users.